Triple Keys for High Security
Very secure and highly efficient: encryption and decryption with luminescent perovskites
Advertisement
To guarantee high data security, encryption must be unbreakable while the data remains rapidly and easily readable. A novel strategy for optical encryption/decryption of information has now been introduced in the journal Angewandte Chemie by a Chinese research team. It is based on compounds with carefully modulated luminescent properties that change in response to external stimuli.
© Wiley-VCH
The compounds are hybrid two-dimensional organic-inorganic metal-halide perovskites, whose structure consists of inorganic layers formed from lead and iodide ions (linked PbI6 octahedra) with organic cations arranged between them. They are easy to produce, inexpensive, and printable, while demonstrating interesting optoelectronic properties. A team led by Shenlong Jiang, Qun Zhang, and Yi Luo at the University of Science and Technology of China (Hefei) worked with three perovskites with only slight variations in their cations (phenethylammonium lead iodide perovskite (PEA)2PbI4 and its fluoridated (2-F-PEA)2PbI4 and brominated (4-Br-PEA)2PbI4 derivatives). The small differences between these perovskites result in crucial variation in their luminescent properties. At room temperature and under normal light they cannot be differentiated visually. However, they react differently to stimuli.
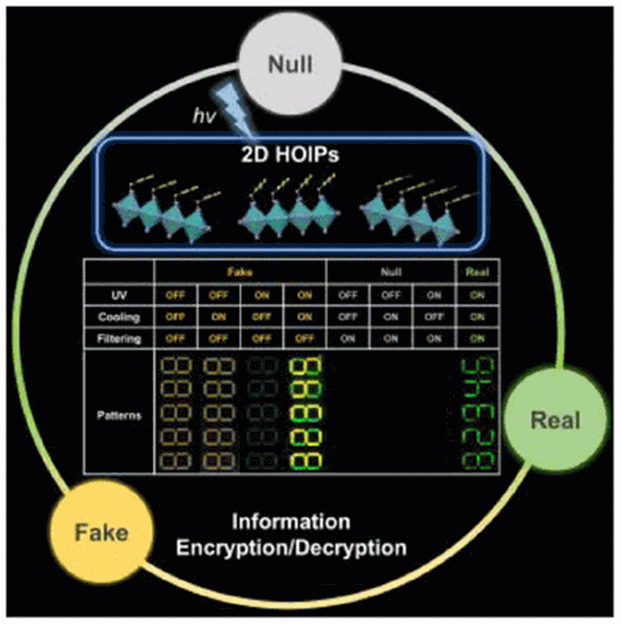
Data encryption with these compounds could look like this example: a “code dictionary” is generated, in which every letter of the alphabet is coded and printed as a matrix of 2x2 dots in a specific arrangement of the three different perovskites. This arrangement allows for about 1047 possible random variants, too many for the encryption to be cracked by even the fastest supercomputer. Decryption of the information requires a combination of three different “keys”: these entail measurement of the luminescence of the individual dot patterns 1) under UV light, 2) upon cooling with liquid nitrogen, and 3) under narrow-bandpass filtering (only a small range of wavelengths is allowed through the filter). Under simultaneous application of keys 1 and 2 (UV light and cooling) dots made of perovskites 1 and 2 glow green and perovskite 3 is yellow. If key 3 (the filter) is applied, dots made of perovskites 1 and 3 both appear green, dots of perovskite 2 become invisible at all. An adequate application of the three keys enables the decryption of the correct pattern, and can then be translated back using the code dictionary.
Alternatively, letters and other symbols can be converted into ASCII codes (8-bit patterns) and encrypted in the form of 2-bit codes. To do this, the four possible combinations of 0 and 1 (00, 01, 10, 11) are encrypted as randomly chosen 3x3 dot matrices. The true patterns are hidden among a large number of false, unassignable patterns. Decryption again uses the three keys. The false dot patterns can efficiently be removed by computer and the remaining 2-bit codes assembled into 8-bit ASCII codes, which can be translated back into symbols.
This method based on different luminescent perovskites in combination with the facile implementation of the triple keys and the dot matrix patterns opens new possibilities for improved data security with rapid, efficient decryption.